Вы используете устаревший браузер. Этот и другие сайты могут отображаться в нем неправильно.
Необходимо обновить браузер или попробовать использовать другой.
Необходимо обновить браузер или попробовать использовать другой.
-
🔥 Бесплатный курс от Академии Кодебай: «Анализ защищенности веб-приложений»
🛡 Научитесь находить и использовать уязвимости веб-приложений.
🧠 Изучите SQLi, XSS, CSRF, IDOR и другие типовые атаки на практике.
🧪 Погрузитесь в реальные лаборатории и взломайте свой первый сайт!
🚀 Подходит новичкам — никаких сложных предварительных знаний не требуется.Доступ открыт прямо сейчас — Записаться бесплатно
Аудит безопасности
Статья SSH аудит
Окт 11
- 4 659
- 2
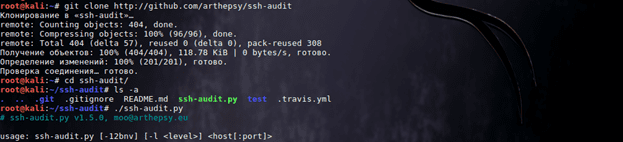
Всем привет! Хочу ознакомить вас с одним любопытным инструментом, который возможно пригодится в фазе сбора информации. Называется он SSH-audit.

Общая информация о программе.
Изменения в версии v1.0.20160917 SSH-аудит:
· Создание тестов для сравнения Dropbear SSH версий.
Dropbear - это реализация SSH 2 для систем с ограниченным объёмом оперативной памяти, пригодная для большинства задач по защите передачи данных. В ней реализованы все основные компоненты протокола SSH 2, а также поддержка X11 и туннелирование аутентификации (для использования локальных ключей при установлении соединения с удалённого сервера)
· Добавлен Prospector (Python Static Analysis) возможность конфигурации и запуска скрипта.
· Подпись mpint.
· Реализация сравнения версий OpenSSH.
· Bump version.
Установим утилиту:
> git clone http://github.com/arthepsy/ssh-audit
Перейдем в папку и запустим исполняемый...
Общая информация о программе.
Изменения в версии v1.0.20160917 SSH-аудит:
· Создание тестов для сравнения Dropbear SSH версий.
Dropbear - это реализация SSH 2 для систем с ограниченным объёмом оперативной памяти, пригодная для большинства задач по защите передачи данных. В ней реализованы все основные компоненты протокола SSH 2, а также поддержка X11 и туннелирование аутентификации (для использования локальных ключей при установлении соединения с удалённого сервера)
· Добавлен Prospector (Python Static Analysis) возможность конфигурации и запуска скрипта.
· Подпись mpint.
· Реализация сравнения версий OpenSSH.
· Bump version.
Установим утилиту:
> git clone http://github.com/arthepsy/ssh-audit
Перейдем в папку и запустим исполняемый...
Статья VOIP Security Audit Framework
Окт 08
- 5 824
- 5
Всем привет! В этой статье я покажу, как провести аудит безопасности систем IP-телефонии.
Для начала необходимо заиметь то, что мы будем проверять, для этого подойдет дистрибутив FreePBX, объясню, что это:
FreePBX - представляет собой веб-ориентированный GUI с открытым исходным кодом, который используется для контроля и управления Asterisk (PBX), - open source сервер связи. Распространяется под лицензией GNU - лицензии с открытым исходным кодом. Данный программный пакет может быть установлен вручную или в составе предварительно сконфигурированного дистрибутива FreePBX, в который входят: операционная система, Asterisk и FreePBX GUI с соблюдением всех зависимостей, для его скачивания перейдем по ссылке =>
Скачаем ISO, устанавливаем систему в Oracle VM VirtualBox, к примеру.

По адресу 192.168.0.109 будет доступен web интерфейс, для управления и настройки сервера. Перейдем по нему...
Для начала необходимо заиметь то, что мы будем проверять, для этого подойдет дистрибутив FreePBX, объясню, что это:
FreePBX - представляет собой веб-ориентированный GUI с открытым исходным кодом, который используется для контроля и управления Asterisk (PBX), - open source сервер связи. Распространяется под лицензией GNU - лицензии с открытым исходным кодом. Данный программный пакет может быть установлен вручную или в составе предварительно сконфигурированного дистрибутива FreePBX, в который входят: операционная система, Asterisk и FreePBX GUI с соблюдением всех зависимостей, для его скачивания перейдем по ссылке =>
Ссылка скрыта от гостей
Скачаем ISO, устанавливаем систему в Oracle VM VirtualBox, к примеру.
По адресу 192.168.0.109 будет доступен web интерфейс, для управления и настройки сервера. Перейдем по нему...
Статья Брутфорс веб-сайтов с Hydra (часть вторая инструкции по Hydra)
Авг 17
- 22 503
- 3
Первая часть здесь: «THC-Hydra: очень быстрый взломщик сетевого входа в систему». Рекомендуется начать знакомство именно с неё, т. к. она содержит подробное описание синтаксиса и инструкцию по работе с Hydra.
В этой части рассмотрены трудные моменты по перебору паролей на веб-сайтах. Трудными они являются из-за того, что все веб-сайты разные и содержат разные поля в формах. А названия этих полей нужно обязательно указать в Hydra. Более того, даже если указать всё правильно, это не означает, что Hydra будет работать корректно — в Интернете (в том числе англоязычном) очень много вопросов по этому поводу. В этой части будут рассмотрены эти проблемы и даны рекомендации как правильно настроить Hydra для перебора паролей на сайтах.
Помощь по модулям http-post-form и http-get-form
По умолчанию эти модули...
В этой части рассмотрены трудные моменты по перебору паролей на веб-сайтах. Трудными они являются из-за того, что все веб-сайты разные и содержат разные поля в формах. А названия этих полей нужно обязательно указать в Hydra. Более того, даже если указать всё правильно, это не означает, что Hydra будет работать корректно — в Интернете (в том числе англоязычном) очень много вопросов по этому поводу. В этой части будут рассмотрены эти проблемы и даны рекомендации как правильно настроить Hydra для перебора паролей на сайтах.
Помощь по модулям http-post-form и http-get-form
По умолчанию эти модули...
Статья Списки слов для атаки по словарю: пароли, имена пользователей, каталоги
Авг 15
- 18 600
- 1
Далеко не всё программное обеспечение содержит эксплуатируемые уязвимости (как этого хотелось бы некоторым). Но цепь, как известно, рвётся на самом слабом звене. И нам не важно, насколько сильны остальные звенья, если мы найдём слабое.
Очень часто слабым звеном является человек. Именно поэтому достаточно популярен социальный инжениринг. Ещё один вид атаки, который я бы также отнёс к человеческому фактору, это атака на слабые пароли. Как стало известно из недавних новостей, даже некоторые профессионалы в безопасности компьютерной информации, самые настоящие хакеры, иногда используют слабые пароли.
Атаки на пароль можно разделить на две большие группы: атаку на хеш и попытку подобрать пароль для аутентификации. Не будем останавливаться подробно на их характеристиках, для данной статьи это несущественно. Поскольку в обеих группах возможна атака по словарю...
Очень часто слабым звеном является человек. Именно поэтому достаточно популярен социальный инжениринг. Ещё один вид атаки, который я бы также отнёс к человеческому фактору, это атака на слабые пароли. Как стало известно из недавних новостей, даже некоторые профессионалы в безопасности компьютерной информации, самые настоящие хакеры, иногда используют слабые пароли.
Атаки на пароль можно разделить на две большие группы: атаку на хеш и попытку подобрать пароль для аутентификации. Не будем останавливаться подробно на их характеристиках, для данной статьи это несущественно. Поскольку в обеих группах возможна атака по словарю...
Статья SQL-инъекции: простое объяснение для начинающих (часть 1)
Авг 05
- 23 072
- 8
Суть SQL-инъекций
Наверное, уже слышали шутку из Интернета: «Почему во всех уроках рисования одно и тоже: Например, урок по рисованию совы. Сначала полчаса долго в деталях рисуем глаз совы. А потом — раз — за пять минут — рисуем оставшуюся часть совы».
Вот даже картинка по этому поводу есть:

По SQL-инжектам материала море: статьи, книги, видеокурсы (платные и бесплатные). При этом не многие из них прибавляют понимания по этому вопросу. Особенно если вы новичок. Я хорошо помню свои ощущения: вот он кружок, вот он остаток совы…
Цель этой заметки —натянуть глаз на сову дать нормальное просто объяснение, что же такое SQL-инъекции, в чём заключается их суть, насколько и почему они опасны.
Для опытов, у нас будет очень простой и уязвимый к SQL-инъекции скрипт:
Наверное, уже слышали шутку из Интернета: «Почему во всех уроках рисования одно и тоже: Например, урок по рисованию совы. Сначала полчаса долго в деталях рисуем глаз совы. А потом — раз — за пять минут — рисуем оставшуюся часть совы».
Вот даже картинка по этому поводу есть:
По SQL-инжектам материала море: статьи, книги, видеокурсы (платные и бесплатные). При этом не многие из них прибавляют понимания по этому вопросу. Особенно если вы новичок. Я хорошо помню свои ощущения: вот он кружок, вот он остаток совы…
Цель этой заметки —
Для опытов, у нас будет очень простой и уязвимый к SQL-инъекции скрипт:
HTML:
<!DOCTYPE html>
<html>
<head>
<meta charset="UTF-8">
<title></title>
</head>
<body>...Статья Crunch — генератор паролей: основы использования и практические примеры
Июл 14
- 30 741
- 25
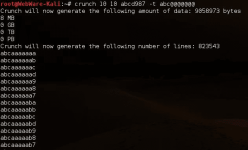
Что такое Crunch
Crunch – генератор словарей паролей, в которых можно определить стандартную или заданную кодировку. Crunch может произвести все возможные комбинации и перестановки.
Особенности:
Методы взламывания пароля...
Crunch – генератор словарей паролей, в которых можно определить стандартную или заданную кодировку. Crunch может произвести все возможные комбинации и перестановки.
Особенности:
- crunch генерирует списки слов (WordList) как методом комбинации, так и методом перестановки
- он может разбить вывод по количеству строк или размеру файла
- поддерживается возобновление процесса после остановки
- образец (паттерн) поддерживает числа и символы
- образец поддерживает по отдельности символы верхнего и нижнего регистра
- работая с несколькими файлами, выводит отчёт о статусе
- новая опция -l для буквальной поддержки, @,% ^
- новая опция -d для ограничения дублирования символов, смотрите man-файл для деталей
- поддержка unicode
Методы взламывания пароля...
Статья Стресс-тест сети: DoS веб-сайта в Kali Linux с GoldenEye
Июн 20
- 29 112
- 1
На страницах codeby.net уже говорилось об инструментах DoS, которые могут сильно нагрузить серверы HTTP, чтобы парализовать их работу из-за исчерпания пула ресурсов. GoldenEye — это ещё один, со своими особенностями, который может положить сервер за 30 секунд, в зависимости от того, насколько велик пул его памяти. Конечно, он не работает на защищённых серверах и серверах за правильно настроенными WAF, IDS. Но это отличный инструмент для тестирования вашего веб-сервера на повышенную нагрузку. А на основании полученных результатов можно изменить правила iptables/файерволов для увеличения устойчивости и сопротивляемости к негативным факторам.
Это интересно:
Это интересно:
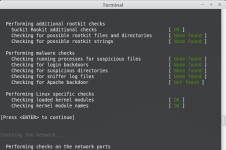
Статья Как сканировать Linux на руткиты (rootkits) с помощью rkhunter
Мар 08
- 5 640
- 1
Руткиты (rootkit) — это вредоносные программы, созданные для получения доступа уровня рута, при этом они прячут своё присутствие от антивирусных программ. Обычно руткиты устнавливаются на вашу систему троянами, содержащимися вместе с загруженными файлами, через известные системные уязвимости, подозрительными приложениями к письмам, при веб-сёрфинге или просто после взлома пароля.
Для Linux есть несколько инструментов сканирования руткитов, которые помогают противостоять известным или потенциальным руткитам. Один из таких инструментов выявления руткитов называется
Установка rkhunter на Linux
Для установки rkhunter на Debian, Ubuntu или Linux Mint:
Для установки rkhunter на Fedora:
Для Linux есть несколько инструментов сканирования руткитов, которые помогают противостоять известным или потенциальным руткитам. Один из таких инструментов выявления руткитов называется
Ссылка скрыта от гостей
. Здесь я опишу, как сканировать системы Linux на наличие руткитов с помощью rkhunter.Установка rkhunter на Linux
Для установки rkhunter на Debian, Ubuntu или Linux Mint:
Код:
$ sudo apt-get install rkhunter
Код:
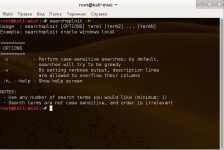
$ sudo yum install...Статья Metasploit Exploitation Framework и searchsploit — как искать и как использовать эксплойты
Янв 09
- 20 271
- 1
Metasploit Exploitation Framework — это инструмент для тестирования на проникновение. Он содержит большую базу эксплойтов, позволяет использовать их прямо из Metasploit. Существует две версии Metasploit, в этом уроке я рассматриваю бесплатную версию.
searchsploit — это инструмент для поиска эксплойтов. Содержит базу, по моим наблюдениям, более обширную, чем Metasploit. Но не содержит функции использования эксплойтов.
На всякий случай, разберёмся с терминологией. Эксплойт – это готовая программа, которая, используя конкретную уязвимость, автоматизирует процесс проникновения или повышения прав или другое несанкционированное действие, которое является следствием уязвимости.
Обе программы не сложны, но нужно знать, что и как там делать. Обе эти программы включены в Kali Linux «из коробки». Поэтому, возможно, вас также заинтересуют статьи:
searchsploit — это инструмент для поиска эксплойтов. Содержит базу, по моим наблюдениям, более обширную, чем Metasploit. Но не содержит функции использования эксплойтов.
На всякий случай, разберёмся с терминологией. Эксплойт – это готовая программа, которая, используя конкретную уязвимость, автоматизирует процесс проникновения или повышения прав или другое несанкционированное действие, которое является следствием уязвимости.
Обе программы не сложны, но нужно знать, что и как там делать. Обе эти программы включены в Kali Linux «из коробки». Поэтому, возможно, вас также заинтересуют статьи: