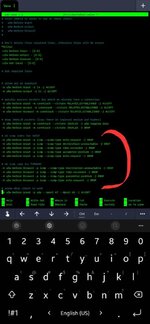
Вот полный конфиг:
Bash:
#
# rules.before
#
# Rules that should be run before the ufw command line added rules. Custom
# rules should be added to one of these chains:
# ufw-before-input
# ufw-before-output
# ufw-before-forward
#
# Don't delete these required lines, otherwise there will be errors
*filter
:ufw-before-input - [0:0]
:ufw-before-output - [0:0]
:ufw-before-forward - [0:0]
:ufw-not-local - [0:0]
# End required lines
# allow all on loopback
-A ufw-before-input -i lo -j ACCEPT
-A ufw-before-output -o lo -j ACCEPT
# quickly process packets for which we already have a connection
-A ufw-before-input -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
-A ufw-before-output -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
-A ufw-before-forward -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
# drop INVALID packets (logs these in loglevel medium and higher)
-A ufw-before-input -m conntrack --ctstate INVALID -j ufw-logging-deny
-A ufw-before-input -m conntrack --ctstate INVALID -j DROP
# ok icmp codes for INPUT
-A ufw-before-input -p icmp --icmp-type echo-request -j DROP
-A ufw-before-input -p icmp --icmp-type destination-unreachable -j ACCEPT
-A ufw-before-input -p icmp --icmp-type time-exceeded -j ACCEPT
-A ufw-before-input -p icmp --icmp-type parameter-problem -j ACCEPT
-A ufw-before-input -p icmp --icmp-type echo-request -j ACCEPT
# ok icmp code for FORWARD
-A ufw-before-forward -p icmp --icmp-type destination-unreachable -j ACCEPT
-A ufw-before-forward -p icmp --icmp-type time-exceeded -j ACCEPT
-A ufw-before-forward -p icmp --icmp-type parameter-problem -j ACCEPT
-A ufw-before-forward -p icmp --icmp-type echo-request -j ACCEPT
# allow dhcp client to work
-A ufw-before-input -p udp --sport 67 --dport 68 -j ACCEPT
#
# ufw-not-local
#
-A ufw-before-input -j ufw-not-local
# if LOCAL, RETURN
-A ufw-not-local -m addrtype --dst-type LOCAL -j RETURN
# if MULTICAST, RETURN
-A ufw-not-local -m addrtype --dst-type MULTICAST -j RETURN
# if BROADCAST, RETURN
-A ufw-not-local -m addrtype --dst-type BROADCAST -j RETURN
# all other non-local packets are dropped
-A ufw-not-local -m limit --limit 3/min --limit-burst 10 -j ufw-logging-deny
-A ufw-not-local -j DROP
# allow MULTICAST mDNS for service discovery (be sure the MULTICAST line above
# is uncommented)
-A ufw-before-input -p udp -d 224.0.0.251 --dport 5353 -j ACCEPT
# allow MULTICAST UPnP for service discovery (be sure the MULTICAST line above
# is uncommented)
-A ufw-before-input -p udp -d 239.255.255.250 --dport 1900 -j ACCEPT
# don't delete the 'COMMIT' line or these rules won't be processed
COMMIT
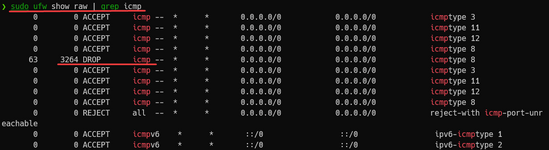
Не выходит тоже(
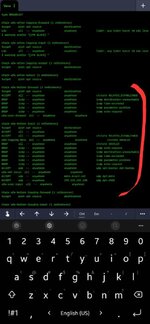
Вот мой iptables
Chain INPUT (policy DROP)
num target prot opt source destination
1 DROP icmp -- anywhere anywhere icmp echo-request
2 ufw-before-logging-input all -- anywhere anywhere
3 ufw-before-input all -- anywhere anywhere
4 ufw-after-input all -- anywhere anywhere
5 ufw-after-logging-input all -- anywhere anywhere
6 ufw-reject-input all -- anywhere anywhere
7 ufw-track-input all -- anywhere anywhere
8 tcp -- anywhere anywhere tcp dpt:ssh ctstate NEW recent: SET name: DEFAULT side: source mask: 255.255.255.255
9 DROP tcp -- anywhere anywhere tcp dpt:ssh ctstate NEW recent: UPDATE seconds: 60 hit_count: 10 name: DEFAULT side: source mask: 255.255.255.255
10 syn_flood tcp -- anywhere anywhere tcp flags:FIN,SYN,RST,ACK/SYN11 DROP tcp -- anywhere anywhere tcp flags:!FIN,SYN,RST,ACK/SYN state NEW
12 DROP all -f anywhere anywhere
13 DROP tcp -- anywhere anywhere tcp flags:FIN,SYN,RST,PSH,ACK,URG/FIN,SYN,RST,PSH,ACK,URG
14 DROP tcp -- anywhere anywhere tcp flags:FIN,SYN,RST,PSH,ACK,URG/NONE
Chain FORWARD (policy DROP)
num target prot opt source destination
1 DROP icmp -- anywhere anywhere icmp echo-request
2 DOCKER-USER all -- anywhere anywhere
3 DOCKER-ISOLATION-STAGE-1 all -- anywhere anywhere
4 ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED
5 DOCKER all -- anywhere anywhere
6 ACCEPT all -- anywhere anywhere
7 ACCEPT all -- anywhere anywhere
8 ufw-before-logging-forward all -- anywhere anywhere
9 ufw-before-forward all -- anywhere anywhere
10 ufw-after-forward all -- anywhere anywhere
11 ufw-after-logging-forward all -- anywhere anywhere
12 ufw-reject-forward all -- anywhere anywhere
13 ufw-track-forward all -- anywhere anywhere
Chain OUTPUT (policy ACCEPT)
num target prot opt source destination
1 DROP icmp -- anywhere anywhere icmp echo-request
2 ufw-before-logging-output all -- anywhere anywhere
3 ufw-before-output all -- anywhere anywhere
4 ufw-after-output all -- anywhere anywhere
5 ufw-after-logging-output all -- anywhere anywhere
6 ufw-reject-output all -- anywhere anywhere
7 ufw-track-output all -- anywhere anywhere
Chain DOCKER (1 references)
num target prot opt source destination
Chain DOCKER-ISOLATION-STAGE-1 (1 references)
num target prot opt source destination
1 DOCKER-ISOLATION-STAGE-2 all -- anywhere anywhere
2 RETURN all -- anywhere anywhere
Chain DOCKER-ISOLATION-STAGE-2 (1 references)
num target prot opt source destination
1 DROP all -- anywhere anywhere
2 RETURN all -- anywhere anywhere
Chain DOCKER-USER (1 references)
num target prot opt source destination
1 RETURN all -- anywhere anywhere
Chain port-scanning (0 references)
num target prot opt source destination
1 RETURN tcp -- anywhere anywhere tcp flags:FIN,SYN,RST,ACK/RST limit: avg 1/sec burst 2
2 DROP all -- anywhere anywhere
Chain syn_flood (1 references)
num target prot opt source destination
1 RETURN all -- anywhere anywhere limit: avg 1/sec burst 3
2 DROP all -- anywhere anywhere
Chain ufw-after-forward (1 references)
num target prot opt source destination
Chain ufw-after-input (1 references)
num target prot opt source destination
1 ufw-skip-to-policy-input udp -- anywhere anywhere udp dpt:netbios-ns
2 ufw-skip-to-policy-input udp -- anywhere anywhere udp dpt:netbios-dgm
3 ufw-skip-to-policy-input tcp -- anywhere anywhere tcp dpt:netbios-ssn
4 ufw-skip-to-policy-input tcp -- anywhere anywhere tcp dpt:microsoft-ds
5 ufw-skip-to-policy-input udp -- anywhere anywhere udp dpt:bootps6 ufw-skip-to-policy-input udp -- anywhere anywhere udp dpt:bootpc7 ufw-skip-to-policy-input all -- anywhere anywhere ADDRTYPE match dst-type BROADCAST
Chain ufw-after-logging-forward (1 references)
num target prot opt source destination
1 LOG all -- anywhere anywhere limit: avg 3/min burst 10 LOG level warning prefix "[UFW BLOCK] "
Chain ufw-after-logging-input (1 references)
num target prot opt source destination
1 LOG all -- anywhere anywhere limit: avg 3/min burst 10 LOG level warning prefix "[UFW BLOCK] "
Chain ufw-after-logging-output (1 references)
num target prot opt source destination
Chain ufw-after-output (1 references)
num target prot opt source destination
Chain ufw-before-forward (1 references)
num target prot opt source destination
1 DROP icmp -- anywhere anywhere icmp echo-request
2 ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED
3 DROP icmp -- anywhere anywhere icmp destination-unreachable
4 DROP icmp -- anywhere anywhere icmp time-exceeded
5 DROP icmp -- anywhere anywhere icmp parameter-problem
6 ufw-user-forward all -- anywhere anywhere
Chain ufw-before-input (1 references)
num target prot opt source destination
1 DROP icmp -- anywhere anywhere icmp echo-request
2 ACCEPT all -- anywhere anywhere
3 ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED
4 ufw-logging-deny all -- anywhere anywhere ctstate INVALID
5 DROP all -- anywhere anywhere ctstate INVALID
6 DROP icmp -- anywhere anywhere icmp destination-unreachable
7 DROP icmp -- anywhere anywhere icmp time-exceeded
8 DROP icmp -- anywhere anywhere icmp parameter-problem
9 ACCEPT udp -- anywhere anywhere udp spt:bootps dpt:bootpc
10 ufw-not-local all -- anywhere anywhere
11 ACCEPT udp -- anywhere mdns.mcast.net udp dpt:mdns
12 ACCEPT udp -- anywhere 239.255.255.250 udp dpt:1900
13 ufw-user-input all -- anywhere anywhere
Chain ufw-before-logging-forward (1 references)
num target prot opt source destination
Chain ufw-before-logging-input (1 references)
num target prot opt source destination
Chain ufw-before-logging-output (1 references)
num target prot opt source destination
Chain ufw-before-output (1 references)
num target prot opt source destination
1 ACCEPT all -- anywhere anywhere
2 ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED
3 ufw-user-output all -- anywhere anywhere
Chain ufw-logging-allow (0 references)
num target prot opt source destination
1 LOG all -- anywhere anywhere limit: avg 3/min burst 10 LOG level warning prefix "[UFW ALLOW] "
Chain ufw-logging-deny (2 references)
num target prot opt source destination
1 RETURN all -- anywhere anywhere ctstate INVALID limit: avg 3/min burst 10
2 LOG all -- anywhere anywhere limit: avg 3/min burst 10 LOG level warning prefix "[UFW BLOCK] "
Chain ufw-not-local (1 references)
num target prot opt source destination
1 RETURN all -- anywhere anywhere ADDRTYPE match dst-type LOCAL2 RETURN all -- anywhere anywhere ADDRTYPE match dst-type MULTICAST
3 RETURN all -- anywhere anywhere ADDRTYPE match dst-type BROADCAST
4 ufw-logging-deny all -- anywhere anywhere limit: avg 3/min burst 10
5 DROP all -- anywhere anywhere
Chain ufw-reject-forward (1 references)
num target prot opt source destination
Chain ufw-reject-input (1 references)
num target prot opt source destination
Chain ufw-reject-output (1 references)
num target prot opt source destination
Chain ufw-skip-to-policy-forward (0 references)
num target prot opt source destination
1 DROP all -- anywhere anywhere
Chain ufw-skip-to-policy-input (7 references)
num target prot opt source destination
1 DROP all -- anywhere anywhere
Chain ufw-skip-to-policy-output (0 references)
num target prot opt source destination
1 ACCEPT all -- anywhere anywhere
Chain ufw-track-forward (1 references)
num target prot opt source destination
Chain ufw-track-input (1 references)
num target prot opt source destination
Chain ufw-track-output (1 references)
num target prot opt source destination
1 ACCEPT tcp -- anywhere anywhere ctstate NEW
2 ACCEPT udp -- anywhere anywhere ctstate NEW
Chain ufw-user-forward (1 references)
num target prot opt source destination
Chain ufw-user-input (1 references)
num target prot opt source destination
1 ACCEPT tcp -- anywhere anywhere tcp dpt:64327
2 ACCEPT udp -- anywhere anywhere udp dpt:64327
3 ACCEPT tcp -- anywhere anywhere tcp dpt:8443
4 ACCEPT tcp -- anywhere anywhere tcp dpt:https
Chain ufw-user-limit (0 references)
num target prot opt source destination
1 LOG all -- anywhere anywhere limit: avg 3/min burst 5 LOG
level warning prefix "[UFW LIMIT BLOCK] "
2 REJECT all -- anywhere anywhere reject-with icmp-port-unreachable
Chain ufw-user-limit-accept (0 references)
num target prot opt source destination
1 ACCEPT all -- anywhere anywhere
Chain ufw-user-logging-forward (0 references)
num target prot opt source destination
Chain ufw-user-logging-input (0 references)
num target prot opt source destination
Chain ufw-user-logging-output (0 references)
num target prot opt source destination
Chain ufw-user-output (1 references)
num target prot opt source destination